One asset of Apple is that people buy not just one product. Indeed, the compatibility between the Apple products, iOS software, and iCloud makes people want all the Apple products after they bought their first one.
Apple was one of the first and biggest smartphone producers. It also has had a huge influence on the usage of cameras on our devices. But, this isn’t without risk.
Can hackers access your iPhone or iPad camera?
The name that is often used to refer to hacking a (phone) camera is ‘camfecting’.
Camfecting basically means that someone hacks into a camera, without the owner of the device noticing it. It inhibits the potential signals that tell that your camera is on, like a led light or notification. It has been around since at least 2013, when a teenager that won a beauty contest was blackmailed with material obtained from her cameras.
In the last nine years, technology has improved vastly. Camfecting has become a staple for many hackers because it can be easily done and provides the hacker with a ton of information on the person that is subjected to the hack.
How do you hack an Apple camera?
The way that the cameras on your Apple products can be subject to camfecting is through a ‘Trojan horse’ virus. Such a virus is a type of malware that an individual downloads onto an electronic device, since it looks like a legitimate program. So the actual attack is, like the myth goes, dressed up like something else.
How does a hacker convince its subjects to download a Trojan horse? Well, hackers do not only digitally engineer their software, they also use social engineering to convince the victims.
Social engineering refers to a wide range of attacks that play onto the vulnerabilities of human beings. It responds to their likings, feeling of reciprocity, commitment, weakness for authority, or compliance with the social norm. So in short, hackers influence the emotions of individuals so that they download illegitimate software.
After clicking a Trojan horse, not a lot happens in terms of visuals. The malware downloads in the background without opening a page. Therefore, many people think that it is a glitch or an empty file and don’t think too much about it. Still, their devices are infected and hackers will be able to use the cameras on the hacked devices.
While you might be a security expert yourself, even the most alert individuals can fall victim to a Trojan horse exactly because of the social engineering that goes into it. Also, how to create a Trojan horse has become way easier. Before you needed to have elaborate programming knowledge and social engineering knowledge, but Trojan horses can nowadays be easily bought on the dark web.
Differences between the Apple cameras on your products
Apple is known to release a new product every so often. Normally, it doesn’t take a very long time before the latest model becomes outdated. Therefore, the cameras on your specific Apple product will differ from other models.
The older your device is, the more prone it is to be hacked. This has to do with the fact that the older devices don’t get as much attention as the new ones. At some point your Apple device will be unable to update to the latest iOS version, making them more vulnerable.
There are a couple of ways to overcome this, like changing the privacy settings on your Apple products. Also, some more general measures can be taken, like the installation of antivirus software.
The difference between an iPhone and iPad camera
If we compare the cameras between an iPhone and an iPad, the cameras on your iPad are generally of lesser quality than that of the iPhone series. The resolutions are normally lower on both the front and back camera. Also, the zoom function isn’t great, and the camera doesn’t function well in rooms with little light.
Although Apple doesn’t go into the specifics of why this is the case, it implies that the cameras on the iPad are given less attention than the ones on the iPhone. Does this also mean the security aspect receives less attention?
How do you know if someone hacked your iPhone camera?
There are some ways to figure out if someone hacked into the cameras on your Apple products. In case you want to be sure, look out for the following indicators.
Slow or weird performance
If the performance of your device suddenly degrates, it is possible that it is hacked. The spyware that is used to hack runs in the background. This means that it uses battery and memory. In turn, this means that your device acts differently.
Besides that, it can also result in the fact that your device doesn’t act as it’s supposed to. For example, you get a lot of pop-ups, applications are opened at random, or multimedia files start playing without your consent.
Suspicious applications
It could be that your device suddenly has an application that you didn’t install yourself. If these are not familiar to you, make sure to remove them as quickly as possible. Oftentimes, the applications are physically installed by someone else. Therefore, make sure to secure your devices with passwords or fingerprints.
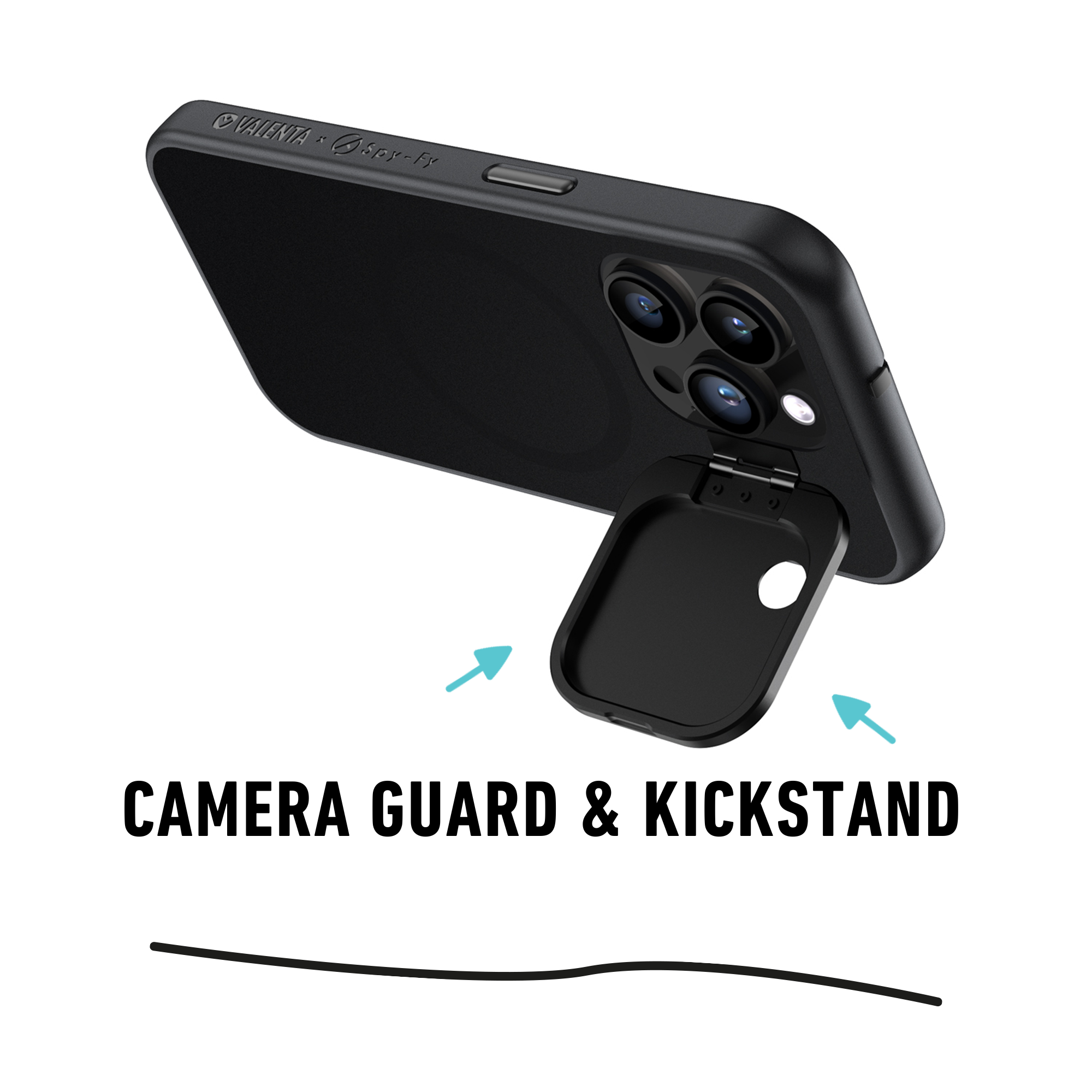
Webcam covers: avoiding hackers from watching your actions
It is easy to avoid people from physically downloading applications on your Apple products. Just add a password. However, it is a bit harder to identify malicious software when it is installed through a Trojan horse.
To avoid hackers from watching you through your cameras, be sure to cover them. With the webcam covers from Spy-Fy you are ascertained that hackers can’t watch your every action. They can be applied to all your devices, including iPhones and iPads. Also, Spy-Fy has a wide range of iPhone privacy cases, including a case for the new iPhone 16 series.