
LinkedIn is a popular tool for job seekers searching for future employment opportunities. However, job seekers should be aware of the potential for scams and phishing attempts on the job platforms ...
How to create a strong password
Making and using a strong password can help to keep your accounts secure from hackers. Far too many of us make one or two passwords that we reuse over and over. We might then use them for multiple ...

Dutch passport cover helps prevent identity fraud. Could this be a global solution?
What do a telescope, CD, and WiFi all have in common? They are all Dutch inventions! The Dutch are known for their cool technology and innovation, and this identity protecting passport cover is no ...

Digital Privacy in America: 10 Key Takeaways
Now more than ever, the news has been inundated with privacy concerns and red flags that have been raised as the world population has become increasingly reliant on the internet to conduct our dail...

A popular video-sharing social media app has been in the news recently due to data privacy and child safety concerns. This prompts the question, is TikTok safe? What is TikTok? For those who might ...

How to recognize email phishing scams
Email Phishing for a Shark Last week Shark Tank’s Barbara Corcoran was in the news after her office fell victim to an email phishing scam. According to Forbes, Corcoran’s bookkeeper received an ema...

Can my phone be hacked while charging? | Juice Jacking
Charging smartphones at public USB charging stations in places like airports, hotels or the mall may leave travelers at risk for juice jacking. Juice Jacking Many of us are so attached to our smart...

Find real love online - How to spot a Catfish
Dating in the digital age opens up seemingly endless possibilities for finding romance. With Valentine’s Day around the corner – it’s important to remember that dating apps can be misused for digit...

How to promote privacy awareness at your company
In the digital age we live in, privacy awareness has become increasingly relevant. Especially when a lack of privacy awareness can lead to vulnerabilities that may leave personal data or sensitive ...

5 Things You Can Do to Protect your Digital Privacy
In a world where much of our lives are spent online, keeping your personal data secure is paramount. Hackers and cyber criminals can use personal information found online to gain access into your a...

How to use Facebook’s updated Privacy Checkup tool
What is Facebook’s Privacy Checkup?Facebook’s Privacy Checkup tool is meant to help make it easier for users to understand their current privacy and security settings. This includes helping users t...

How Much Does Cybercrime Cost?
By the Year 2021, Losses from Cyber Crimes May Reach Up to $6 Trillion. Just in case you are shocked as indeed you should be, the title you just read is very true. According to a report by Aon, int...

Best Privacy Apps For iPhone. Protect your iPhone's data!
Like any other iPhone user, you probably have lots of private data on your iPhone, like personal photos and, business information, passwords, and personal journals. The best way to protect all of t...

How Do I Make My iPhone Completely Private?
As privacy continues to be a major concern for users of various mobile devices today, iPhone users are not in any way exempt. Data mining and access to personal information have become something th...

The Age of Surveillance Capitalism has Begun.
If you’ve not heard of Shoshana Zuboff, social psychologist and also a former professor at Harvard Business School, then chances are that you may not be very familiar with this term. The term “Surv...

Understanding the Risks of Using Public Charging Stations
Many of us cannot bear to have our phones run out of juice. When the battery runs down, we feel like a part of our lives has been put on hold. That is why we are so eager to charge our phones so we...

How Do I Make My Netflix Profile Private?
Hey! Netflix is just an entertainment platform so why will I want to make my Netflix profile private? We live in a time when practically everything we do that requires an internet connection or dat...
What is IOT and how does it work?
“The Internet of Things (IoT) is a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers and the ability to...

iOS 13 Privacy and Security Features You Should Know
With security and privacy taking center stage in the world of information technology, one of the most important factors anyone should consider when purchasing a mobile device or any kind of IT equi...

Ring Doorbell: Invasion of Privacy?
What! Doorbell an invasion of privacy? Whose privacy exactly? With the constantly escalating privacy wars going on today, the attention of the world has been drawn to the potential privacy issue th...

Webcams are versatile and convenient. They allow us to stay connected to friends and family, make video conferences with our colleagues and much much more. But like all good things in life, there i...

A Consumer's Guide to the California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA) is a new privacy law aimed at protecting California consumers by establishing new privacy rights. The CCPA, also known as AB 375, was put into effect on J...
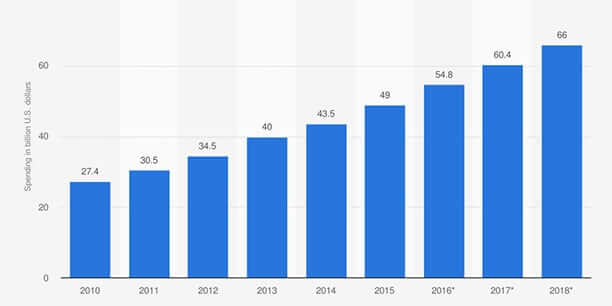
In the past few years, we are witnessing an explosion of data breach cases, cybersecurity and ransomware attacks on small, medium-sized and even big companies. It is very unlikely there will be a d...

How to increase my Android privacy?
Our focus in this article is android privacy since android users are rightfully skeptical about the privacy of their devices. Given that the number of people who use at least one Android device aro...
